There will instances where you will need to set server to be public serving for remote offices requiring access to applications within your network.
FortiOS versions 7 and above offer Geo-IP restriction features, enabling administrators to control access to internal services based on geographical location. This feature is particularly useful for organizations with remote offices or users who need to access applications within the network from specific countries or regions.
By configuring Geo-IP restrictions, you can:
Allow access to internal services only from specific countries or regions.
Restrict access from countries or regions with high security risks.
Comply with data sovereignty regulations by controlling where data is accessed.
Enhance security by limiting exposure to unauthorized access.
To configure Geo-IP restrictions:
1. Login to your Fortigate admin portal, expand Policy and Objects and select Addresses.
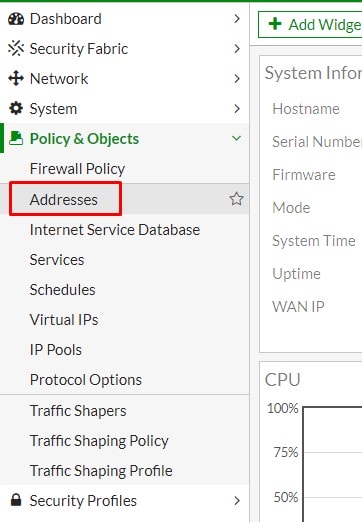
2. Select Create New and select Address.
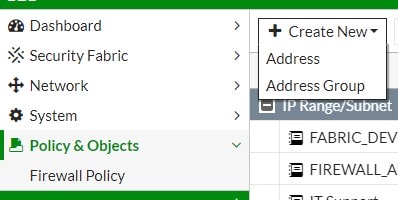
3. Type a name for the location, select Geography from Type dropdown list.
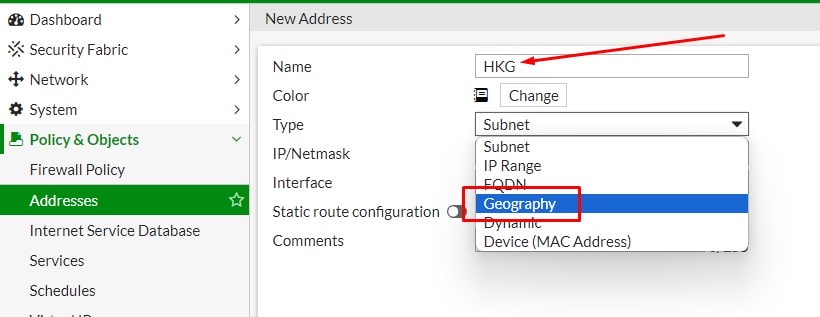
4. Select the country you want to allow.
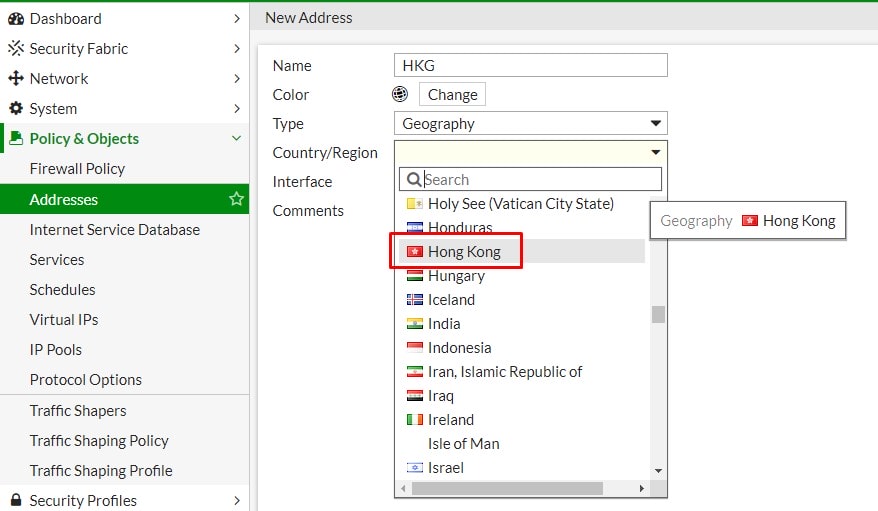
5. Select the interface that this address restriction would apply on.
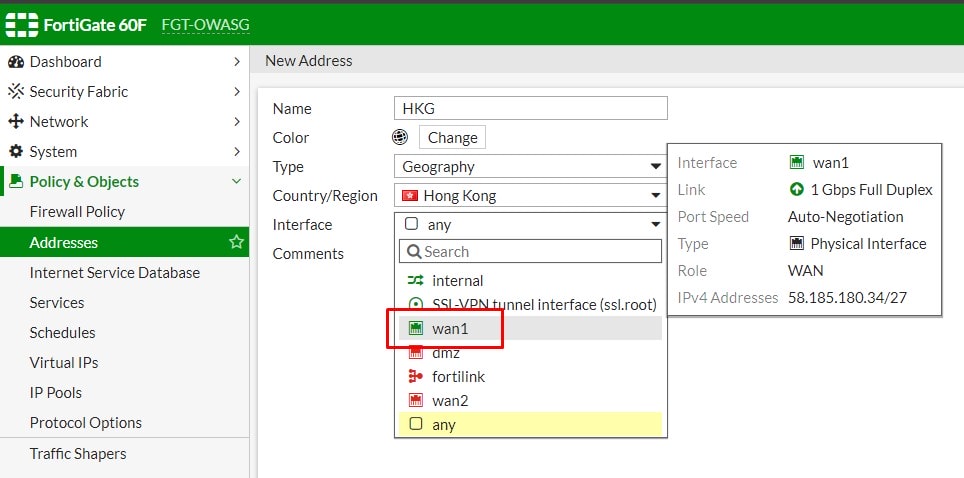
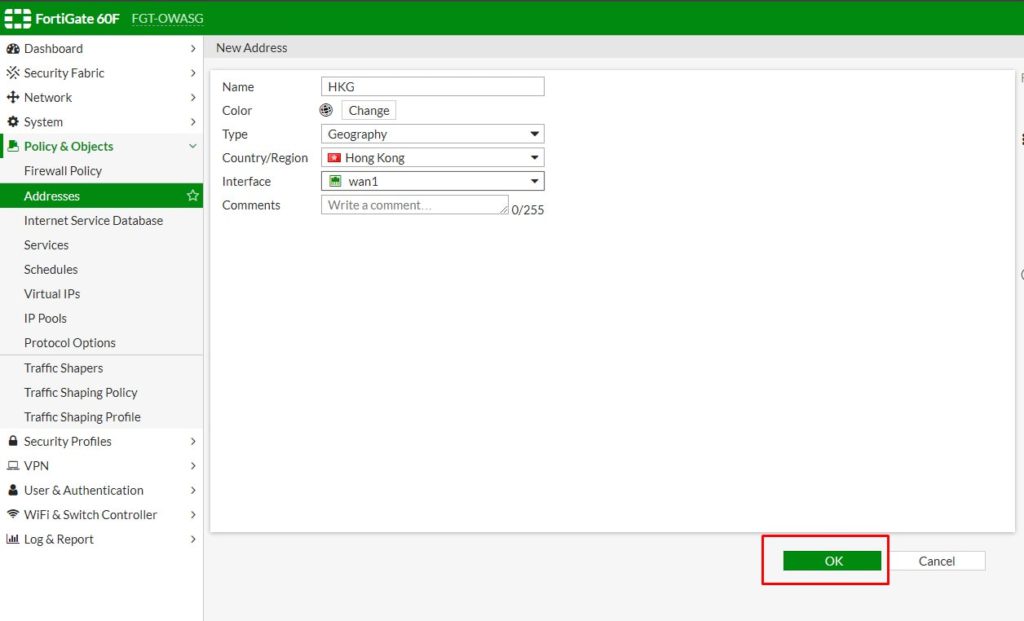
6. Click OK to save.
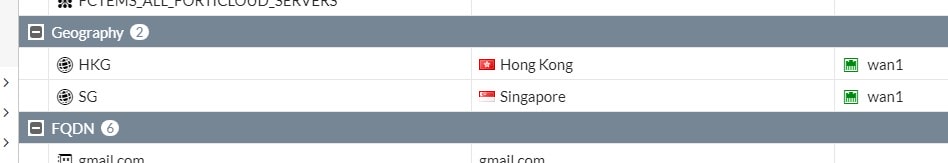
7. Regions added will appear in Geography address group.
8. Apply the policy by select the newly added address to source option of the policy you would like to add the restriction.
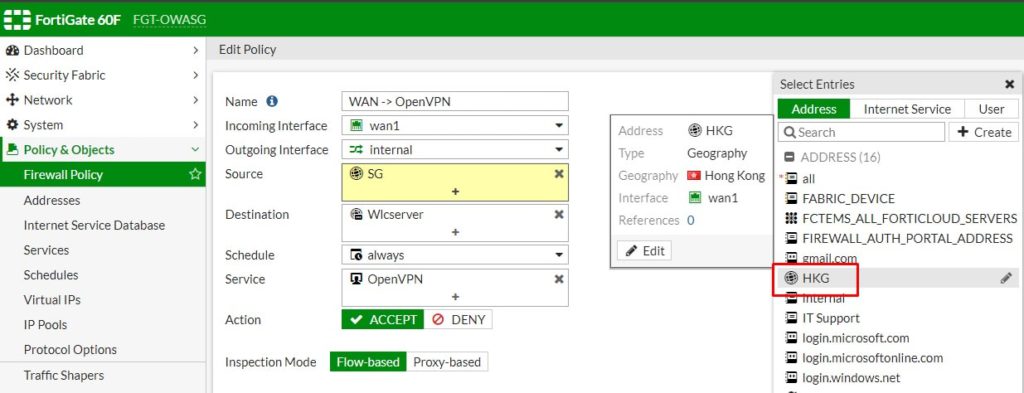
9. Click OK to complete the setup.
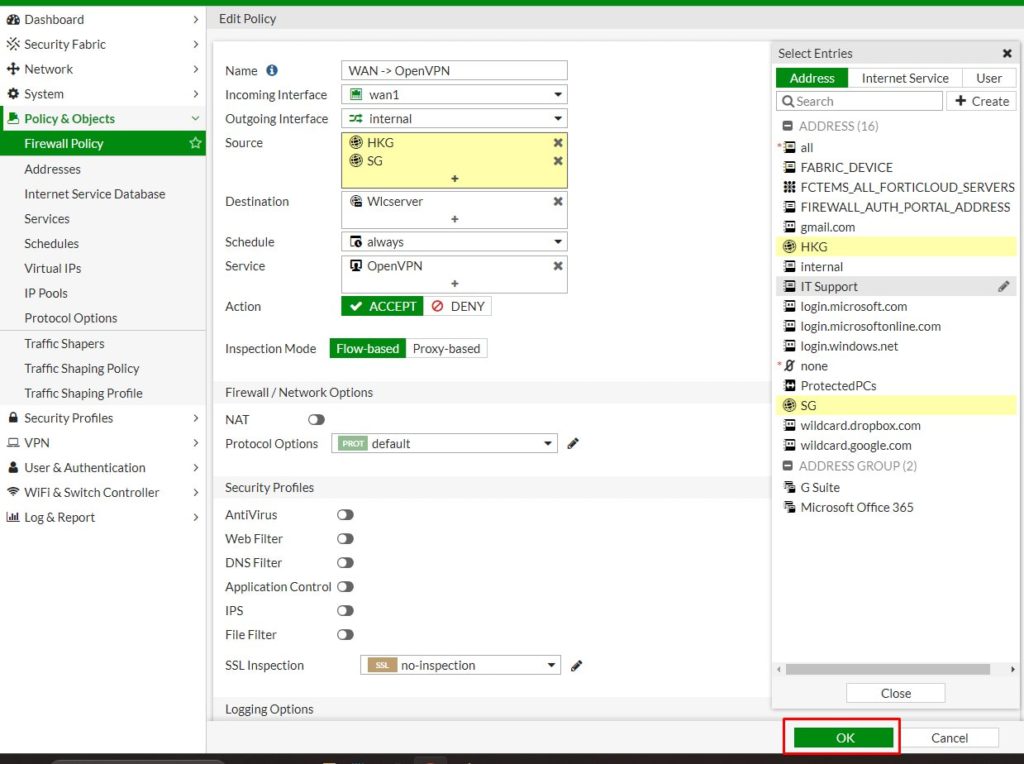
By limiting access to internal services from specific countries or regions, you can reduce unnecessary traffic and prevent bandwidth waste.
Geo-IP restrictions can help block malicious traffic from known botnet sources or countries with high cybercrime activity, reducing the risk of automated attacks.
