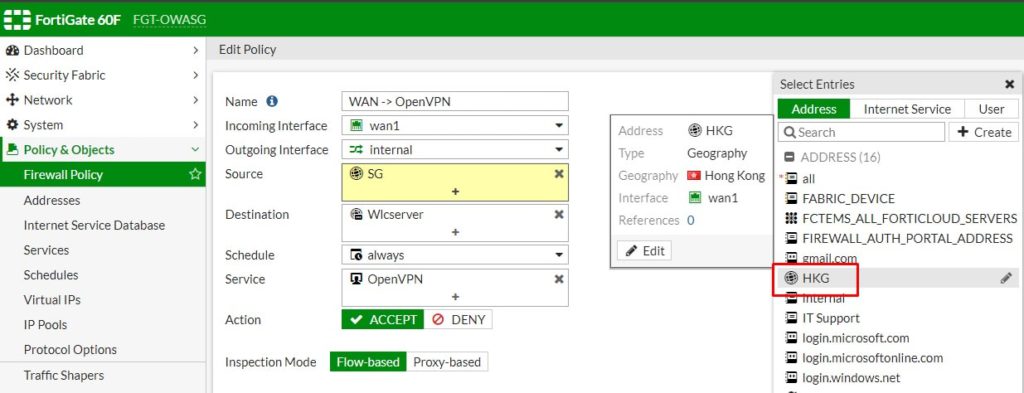
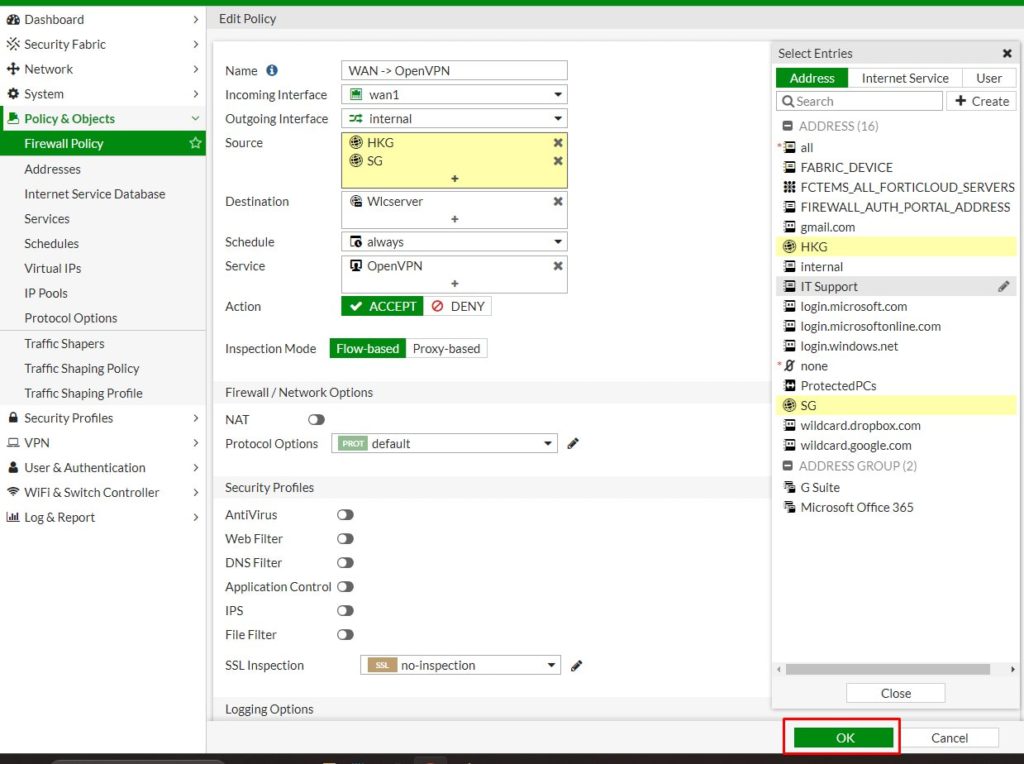
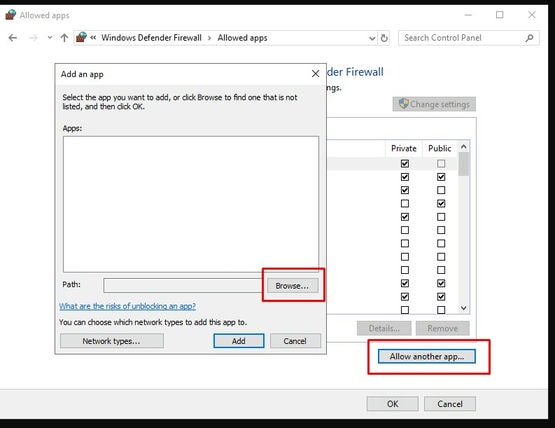
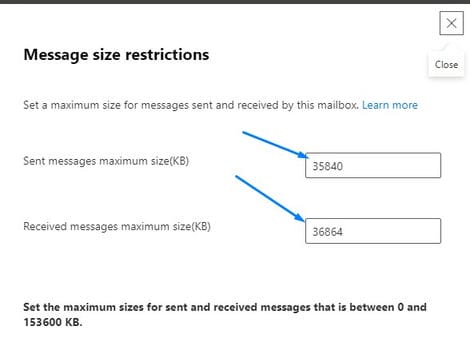
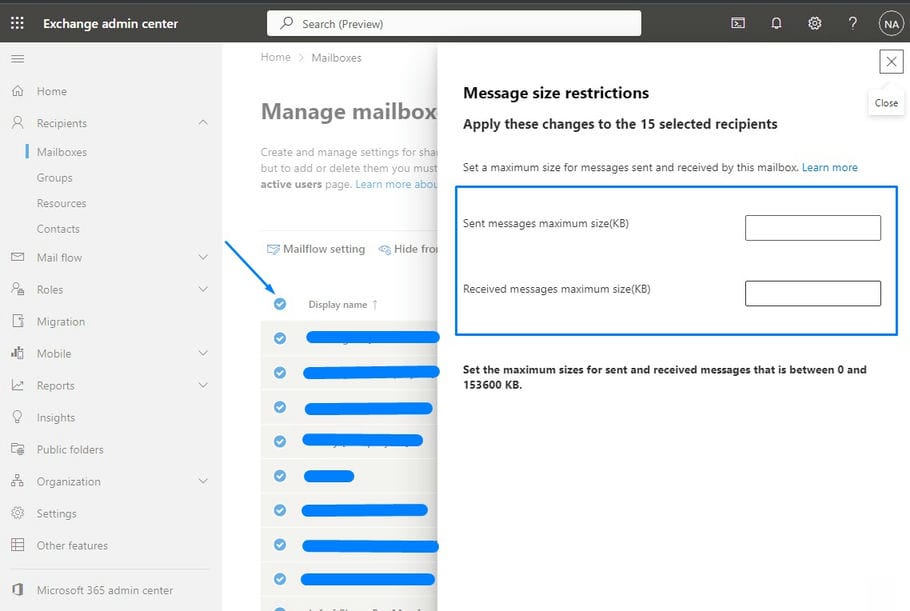
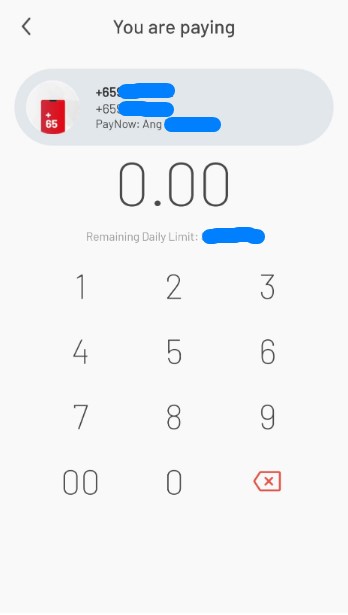
A common issue when accessing shared folders when connecting from remote is forgetting to connect OpenVPN to connect to your office network.
Ideally, OpenVPN should auto connect on startup so that users will not have issue connecting to network share due to this and then subsequently remove the mapping.
One way to get it to run when logged in, is by placing a shortcut in the usual startup folder.
(For all users, %ProgramData%\Microsoft\Windows\Start Menu\Programs\Startup; or for the current user only, %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup.)
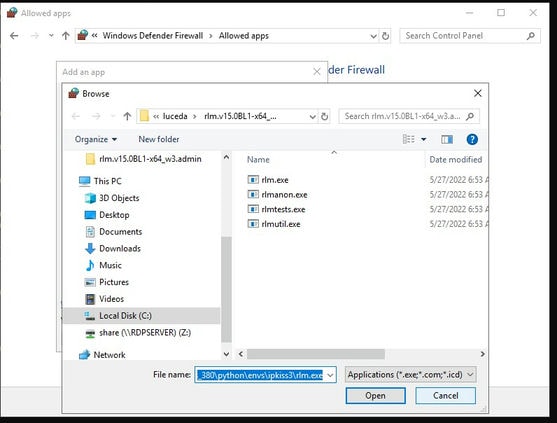
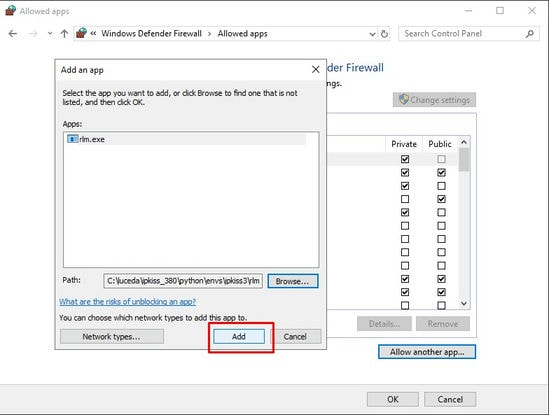
Create shortcut on your desktop pointing to C:\Program Files\OpenVPN\bin\openvpn-gui.exe (verify that the file is located at this location) then cut and paste to either %ProgramData%\Microsoft\Windows\Start Menu\Programs\Startup (current user) or %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup (all users)
or in CMD (current user) type
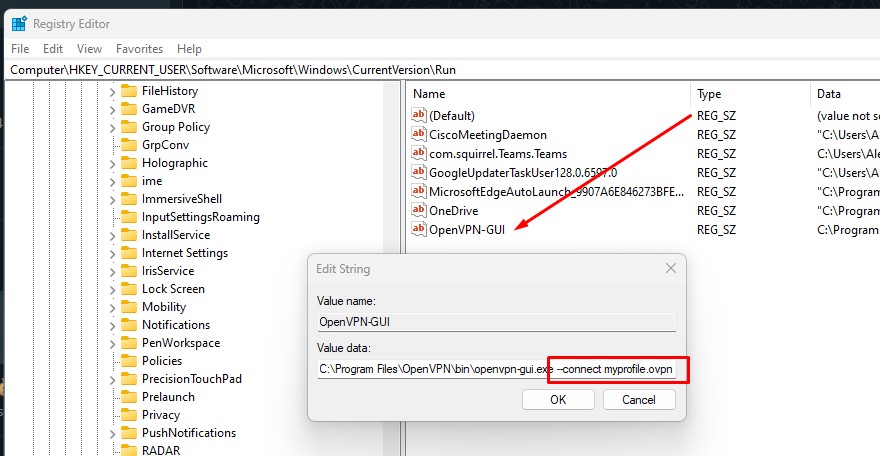
reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v OpenVPN-GUI /t REG_SZ /d \””C:\Program Files\OpenVPN\bin\openvpn-gui.exe –connect myprofile.ovpn\”” /f
replacing myprofile.opvn with the file name of your .opvn profile.
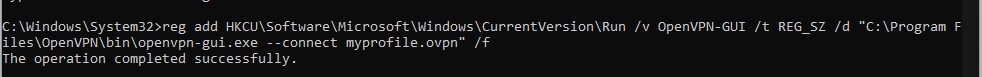
Or you can start regedit, browse to HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run and amend the OpenVPN-GUI data to “C:\Program Files\OpenVPN\bin\openvpn-gui.exe –connect myprofile.ovpn”