01. List all listening TCP ports with “netstat -anp tcp” in administrator’s CMD.
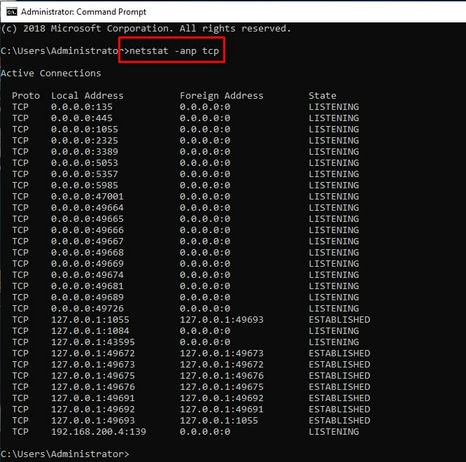
02. Find PID associated with open ports requiring inbound connections.
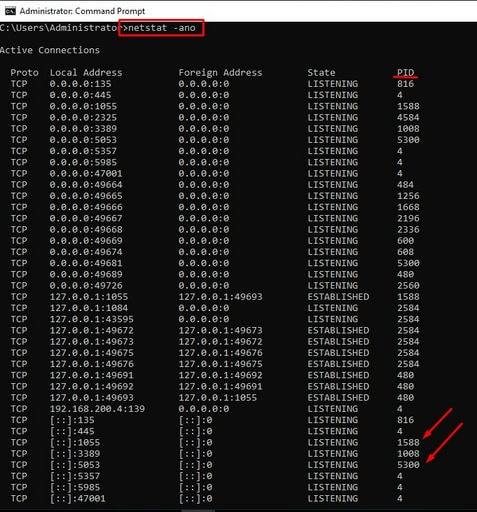
03. Pipe tasklist to find to locate process owner’s name.
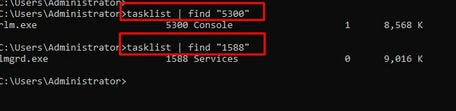
04. User wmic to locate full executable paths of all processes you would like to pass Windows firewall.
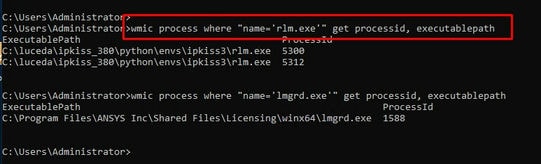
05. Go to Control Panel, All Control Panel Items and select Windows Firewall.
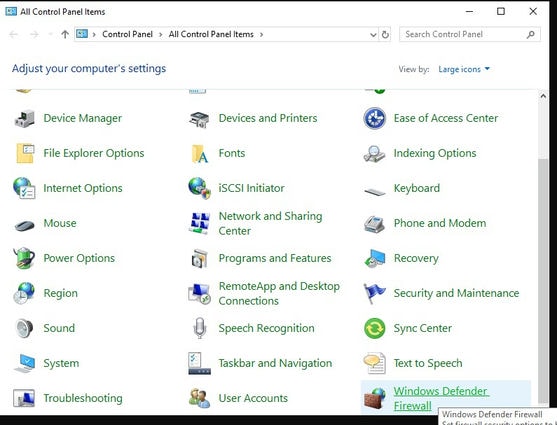
06. Select Allow an app or feature through WIndows Defender Firewall.
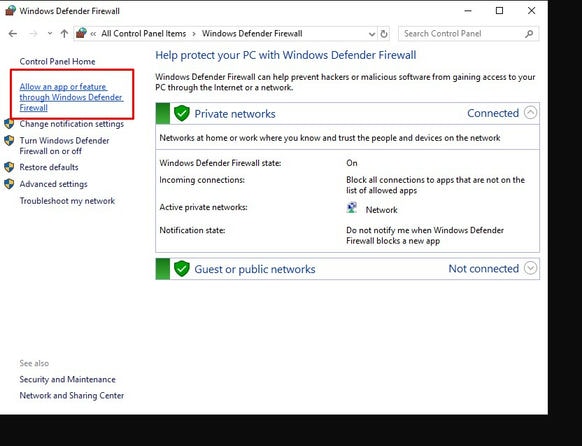
07. Select Allow another app.
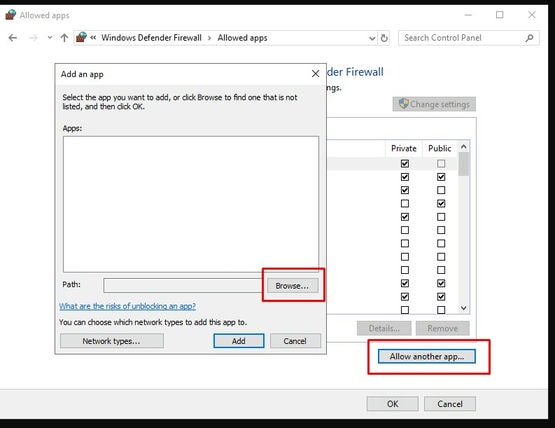
08. Copy from command line process’ full path, paste and click Open.
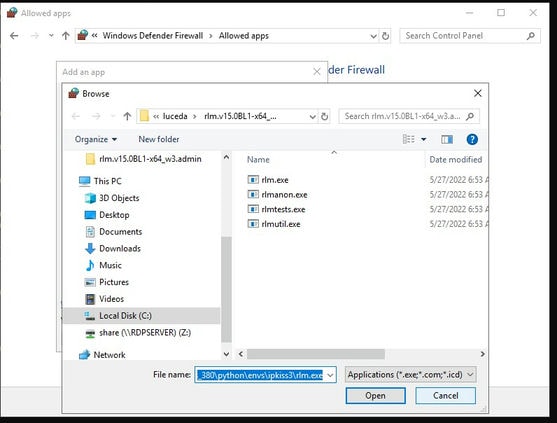
09. Click Add to add the program. Repeat process for all other running processes that are blocked.
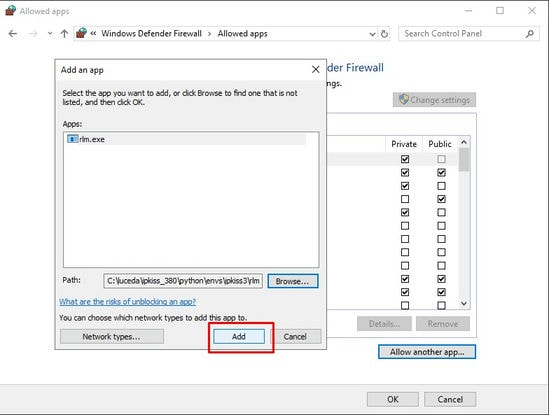
Some applications may dynamically assign ports to listen to for inbound connections, adding the program itself will prevent allowing static ports in while blocking all others used by the process.
